#scrape WhatsApp numbers
Explore tagged Tumblr posts
Text
Precise WhatsApp Number Scraping for Optimized Marketing
With the growing popularity of WhatsApp marketing, there’s been an influx of auxiliary tools on the market. For many marketers, choosing the right software can be a daunting task, often leading to confusion and frustration. Here, we’ll guide you through the key factors to consider when selecting the ideal marketing software.

To illustrate, let’s take the example of selecting scrape WhatsApp numbers software and break down the important points to keep in mind:
Understand Core Features
The first step is to thoroughly evaluate the software’s core features. Many tools claim to offer comprehensive functions but may not align with their advertised capabilities. To avoid this, you can test the software yourself or read detailed user reviews. For instance, some scrape WhatsApp numbers software prioritizes features like mass messaging or account maintenance over robust data scraping, which might not fully address your needs.
Evaluate Ease of Use and Customization
Next, assess how user-friendly the software is and whether it offers customizable options. Taking CrownSoft’s scrape WhatsApp numbers software as an example, it’s designed with simplicity in mind. Users can easily import phone numbers, log into their WhatsApp accounts, and execute scraping tasks efficiently. Additionally, the software allows manual adjustments to customize the scraping depth, enabling you to gather details such as user demographics, profile signatures, and more.
Consider Maintenance and Updates
Frequent updates to WhatsApp mean that auxiliary software must be regularly maintained to ensure compatibility and security. Choosing a tool with reliable after-sales support and consistent updates is crucial to protecting your accounts and ensuring uninterrupted marketing efforts.
Why CrownSoft’s Software Stands Out?
CrownSoft's scrape WhatsApp numbers software offers multiple methods to generate phone numbers for different regions. By logging into your account, the software quickly verifies whether the numbers are registered on WhatsApp. It also provides advanced filtering options, such as recognizing user details like avatars, age, gender, and profile signatures. Exporting the data is straightforward, with formats including .txt, .xls, .xlsx, and .vcf.
In conclusion, selecting the right scrape WhatsApp numbers software involves understanding its features, usability, and maintenance. With tools like CrownSoft’s, you can streamline your marketing efforts and achieve better results. Thank you for reading! If you have further questions or need more details, feel free to reach out.
#CrownSoft's scrape WhatsApp numbers software#scrape WhatsApp numbers software#scrape WhatsApp numbers#whatsapp marketing#whatsapp
0 notes
Text
Updated Personal Infosec Post
Been awhile since I've had one of these posts part deus: but I figure with all that's going on in the world it's time to make another one and get some stuff out there for people. A lot of the information I'm going to go over you can find here:
https://www.privacyguides.org/en/tools/
So if you'd like to just click the link and ignore the rest of the post that's fine, I strongly recommend checking out the Privacy Guides. Browsers: There's a number to go with but for this post going forward I'm going to recommend Firefox. I know that the Privacy Guides lists Brave and Safari as possible options but Brave is Chrome based now and Safari has ties to Apple. Mullvad is also an option but that's for your more experienced users so I'll leave that up to them to work out. Browser Extensions:
uBlock Origin: content blocker that blocks ads, trackers, and fingerprinting scripts. Notable for being the only ad blocker that still works on Youtube.
Privacy Badger: Content blocker that specifically blocks trackers and fingerprinting scripts. This one will catch things that uBlock doesn't catch but does not work for ads.
Facebook Container: "but I don't have facebook" you might say. Doesn't matter, Meta/Facebook still has trackers out there in EVERYTHING and this containerizes them off away from everything else.
Bitwarden: Password vaulting software, don't trust the password saving features of your browsers, this has multiple layers of security to prevent your passwords from being stolen.
ClearURLs: Allows you to copy and paste URL's without any trackers attached to them.
VPN: Note: VPN software doesn't make you anonymous, no matter what your favorite youtuber tells you, but it does make it harder for your data to be tracked and it makes it less open for whatever public network you're presently connected to.
Mozilla VPN: If you get the annual subscription it's ~$60/year and it comes with an extension that you can install into Firefox.
Mullvad VPN: Is a fast and inexpensive VPN with a serious focus on transparency and security. They have been in operation since 2009. Mullvad is based in Sweden and offers a 30-day money-back guarantee for payment methods that allow it.
Email Provider: Note: By now you've probably realized that Gmail, Outlook, and basically all of the major "free" e-mail service providers are scraping your e-mail data to use for ad data. There are more secure services that can get you away from that but if you'd like the same storage levels you have on Gmail/Ol utlook.com you'll need to pay.
Tuta: Secure, end-to-end encrypted, been around a very long time, and offers a free option up to 1gb.
Mailbox.org: Is an email service with a focus on being secure, ad-free, and privately powered by 100% eco-friendly energy. They have been in operation since 2014. Mailbox.org is based in Berlin, Germany. Accounts start with up to 2GB storage, which can be upgraded as needed.
Email Client:
Thunderbird: a free, open-source, cross-platform email, newsgroup, news feed, and chat (XMPP, IRC, Matrix) client developed by the Thunderbird community, and previously by the Mozilla Foundation.
FairMail (Android Only): minimal, open-source email app which uses open standards (IMAP, SMTP, OpenPGP), has several out of the box privacy features, and minimizes data and battery usage.
Cloud Storage:
Tresorit: Encrypted cloud storage owned by the national postal service of Switzerland. Received MULTIPLE awards for their security stats.
Peergos: decentralized and open-source, allows for you to set up your own cloud storage, but will require a certain level of expertise.
Microsoft Office Replacements:
LibreOffice: free and open-source, updates regularly, and has the majority of the same functions as base level Microsoft Office.
OnlyOffice: cloud-based, free
FreeOffice: Personal licenses are free, probably the closest to a fully office suite replacement.
Chat Clients: Note: As you've heard SMS and even WhatsApp and some other popular chat clients are basically open season right now. These are a couple of options to replace those. Note2: Signal has had some reports of security flaws, the service it was built on was originally built for the US Government, and it is based within the CONUS thus is susceptible to US subpoenas. Take that as you will.
Signal: Provides IM and calling securely and encrypted, has multiple layers of data hardening to prevent intrusion and exfil of data.
Molly (Android OS only): Alternative client to Signal. Routes communications through the TOR Network.
Briar: Encrypted IM client that connects to other clients through the TOR Network, can also chat via wifi or bluetooth.
SimpleX: Truly anonymous account creation, fully encrypted end to end, available for Android and iOS.
Now for the last bit, I know that the majority of people are on Windows or macOS, but if you can get on Linux I would strongly recommend it. pop_OS, Ubuntu, and Mint are super easy distros to use and install. They all have very easy to follow instructions on how to install them on your PC and if you'd like to just test them out all you need is a thumb drive to boot off of to run in demo mode. For more secure distributions for the more advanced users the options are: Whonix, Tails (Live USB only), and Qubes OS.
On a personal note I use Arch Linux, but I WOULD NOT recommend this be anyone's first distro as it requires at least a base level understanding of Linux and liberal use of the Arch Linux Wiki. If you game through Steam their Proton emulator in compatibility mode works wonders, I'm presently playing a major studio game that released in 2024 with no Linux support on it and once I got my drivers installed it's looked great. There are some learning curves to get around, but the benefit of the Linux community is that there's always people out there willing to help. I hope some of this information helps you and look out for yourself, it's starting to look scarier than normal out there.

#infosec#personal information#personal infosec#info sec#firefox#mullvad#vpn#vpn service#linux#linux tails#pop_os#ubuntu#linux mint#long post#whonix#qubes os#arch linux
79 notes
·
View notes
Text
IMPORTANT FOR NEW PHOTOGRAPHERS
SCAM ALERT⚠️‼️
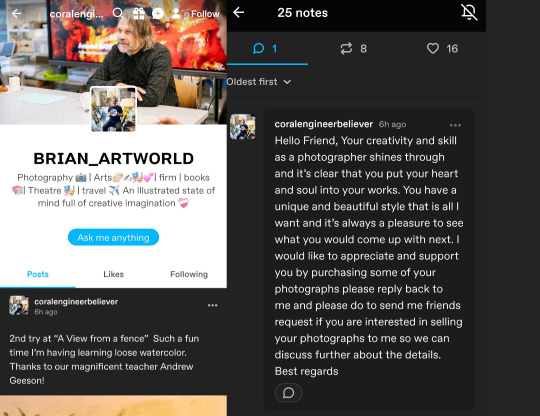
There are bots/scammers replying to photos with promises of buying your work, asking to be DMed.
Three that I have come across in one day are @rogerwil01 @ericcampbell0 and @coralengineerbeliever.
The former solicited a response on a photo post of mine. And the easiest way to know it's scam bots is how it responds to other messages. Another bot responded to the solicitation that rogerwil01 sent with an affirmative, and rogerwil01 sent one back with no idea that the response was not from the blog owner or copyright holder of the photo. These bots are not concerned with copyright, but an actual art dealer very much would be.
They promise naive photographers money, basically. They only target photos that are under 1000 notes, and often go after amateurs with 1-10 notes. These are likely seen as easy targets. Here are some examples of the types of messages they spam.

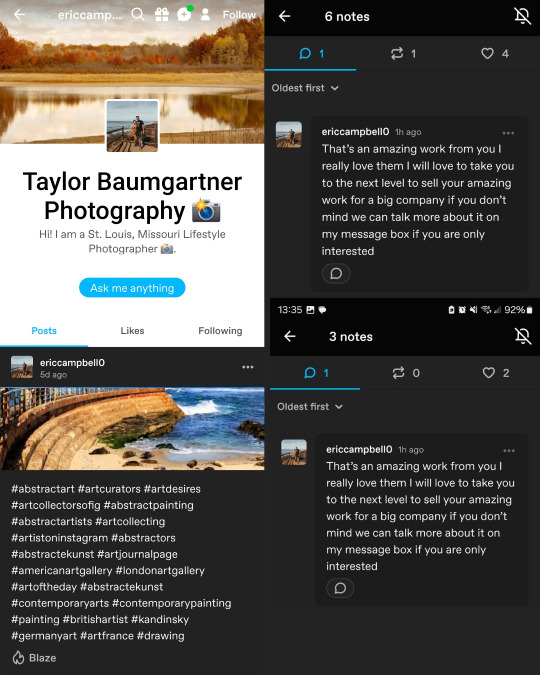
Taylor Baumgartner is a real person. She's an amateur child photographer based in Missouri. But this blog is not her. These mimic actual people to seem legit. A big giveaway is that the url is a totally different name, and a man's one at that. The number on the end is also a hint. These blogs usually have one or two posts of their "original photos" to seem active and real. The tags are usually unrelated or irrelevant. A seaside landscape is not abstract, for example. Nor is it art, exactly.
Also, these accounts have a script and send identical messages, like so...

Here is two bots talking:

A bot solicited another scammer/bot's photo post. Hilarity ensues. I wish I had screenshotted them doing it on my post. But the moment I called rogerwil01 out as being a scammer, he promptly deleted his initial comment and 2 replies, leaving my 2 replies and 1 from another bot. It then blocked me.
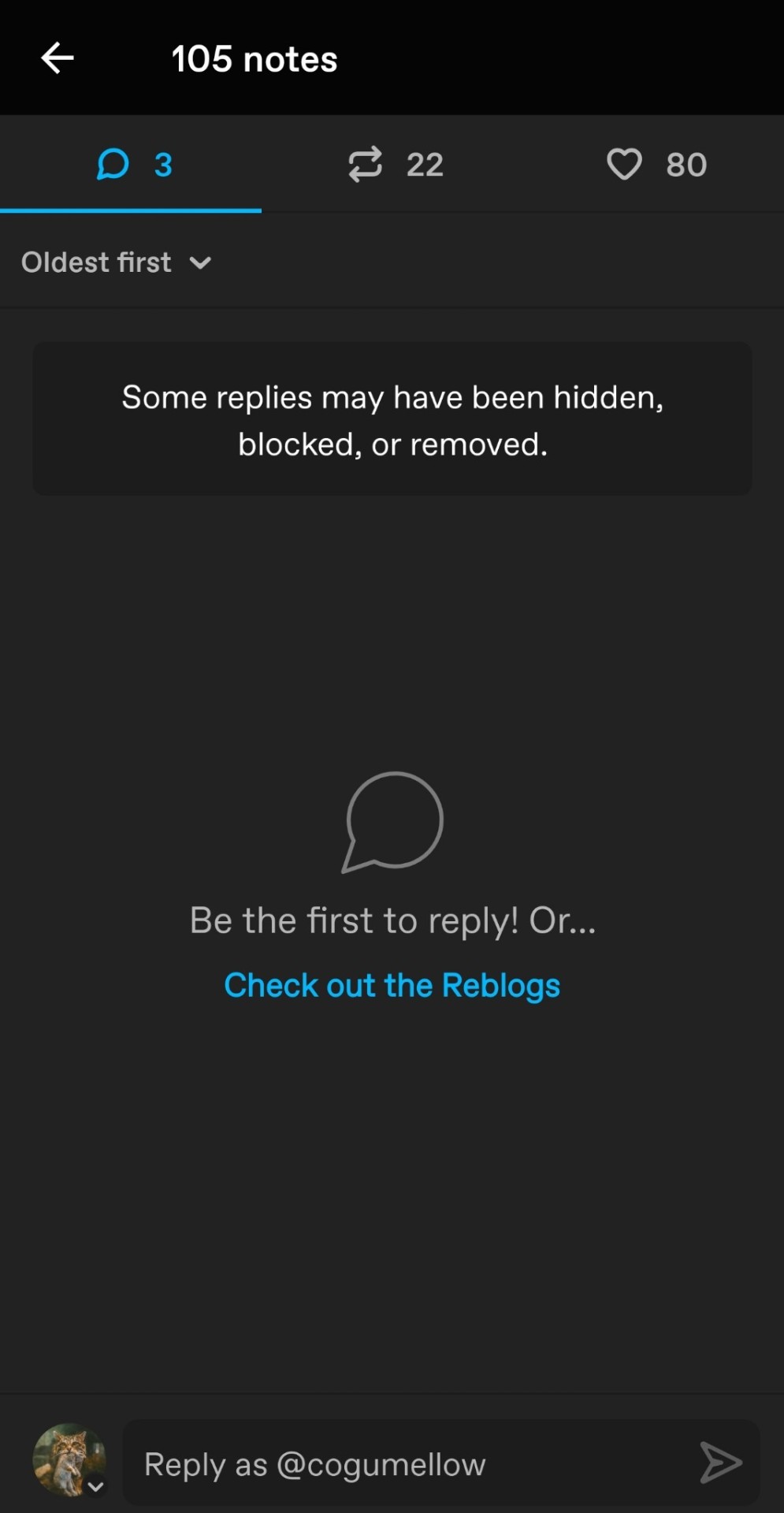
Here's a slightly different scammer. This one mimics an actual artist, but the blog title name is not the same as the name of the artist on the posts that it is reposting. This bot has scraped various real artists' social media accounts, including the prominent Russian artist, Alexey Vaulin, whose likeness the bot has stolen, and the flower paintings and captions are scraped from artist Noemi Cardoso.
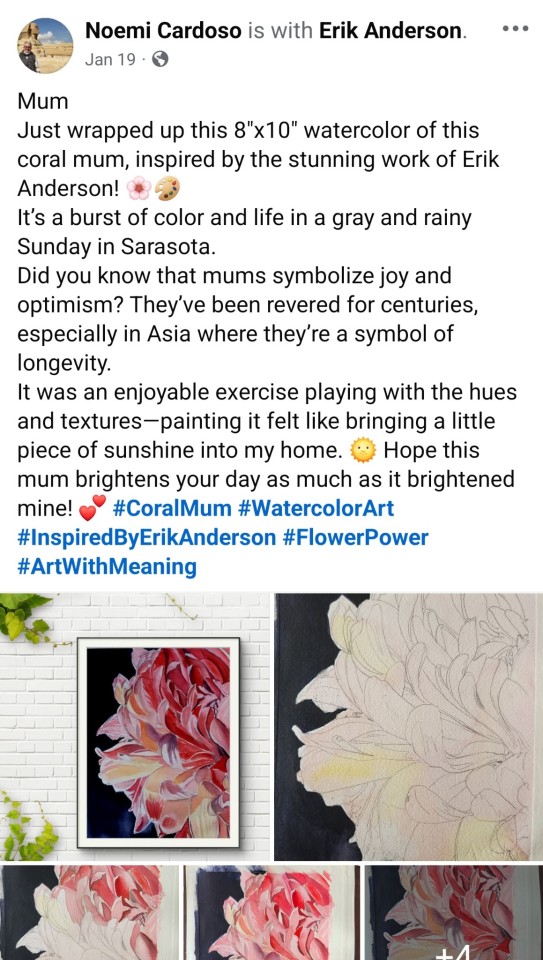
And this is the tactic:
Same idea, just way more words. A big giveaway is soliciting random classical art reblogs. Like this piece by Gentileschi, from 1623. Hilarious. This is not original poster. Again, a huge red flag.
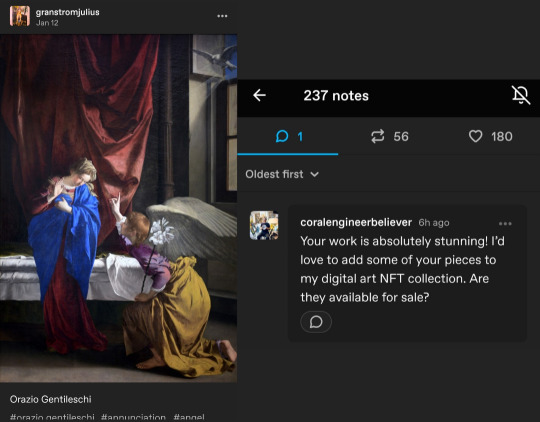
It means that there is literally no human brain behind this. Any human would see that post and know immediately this is a repost of a famous painting by Orazio Gentileschi, not an original piece for sale by OP.
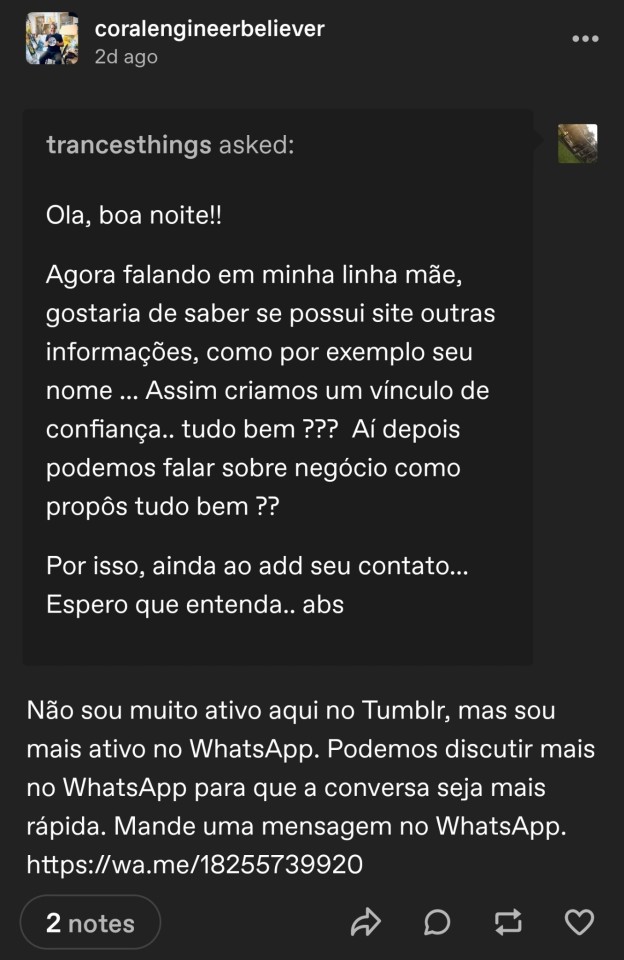
Also, you can see here a DM sent by an interested target (or another bot?) (@trancesthings) seeking more information to get some legitimacy of the scammer. The immediate response from the bot is that they are not active on tumblr (🚩) and to message them instead on WhatsApp (🚩🚩🚩!). No legit company or agent would ever do this. And when asked their name, they would reply. Not say "WhatsApp me!"
Dear fellow photographers, never, ever believe someone soliciting you on tumblr.
A legit contact will send a DM, not a public reply on a post. And they will offer lots of information that proves their legitimacy. But in general, nobody with money is contacting a potential client or artists via tumblr. It's one thing to connect with fellow artists here, but art dealers and publishers will not be scouting tumblr. I would be incredibly suspicious of anybody telling you they want to buy your work or give you money. Period.
If you want your photos to be seen by legitimate agencies and businesses, there are much better websites for that. Including Instagram. (Although that is full of scammers too.) Flickr, 500px, and various stock imagery sites are more legit.
The online photography world is absolutely packed with predators looking to prey on naive amateurs. It's bad enough when they attempt to devalue your work and offer "credit" or "exposure" as payment. I don't know what the deal with these tumblr scams are as I don't engage them, but 100% they are not legit.
Judging by the radio silence from the blogs that received this spam, nobody really believes it and that's awesome. But just in the off-chance there's a young person here posting their photos, and thinks it's a legit offer, I'm posting this warning. Do not engage with these bots.
Delete their replies, report as spam, and block.
#photographers on tumblr#original photographers#photography#photooftheday#curators on tumblr#tumblr photographer#artists on tumblr#photos
4 notes
·
View notes
Text
Phone Number Data: The Digital Identifier Transforming Communication and Business
Introduction In today’s hyper connected digital world, phone numbers have evolved from mere contact points to powerful identifiers that fuel communication, commerce, security, and digital identity. “Phone number data” refers to the information associated with and derived from phone numbers, including their usage, location, metadata, and relationships to user identities. This data has become a valuable asset in sectors ranging from marketing to cybersecurity, but it also poses significant privacy and regulatory challenges. This article explores the meaning of phone number data, its applications, implications, and the future of how this data is used and protected.
What is Phone Number Data?
Phone number data encompasses a wide range of information linked to mobile or landline phone numbers. This can include:
Basic identifiers: Phone number, country code, carrier name, line type (mobile, landline, VoIP).
User metadata: Name, email, location, and other personal identifiers tied to the number.
Usage data: Call logs, text message records, and app interaction history.
Location data: Real-time or historical data based on tower triangulation or GPS (for mobile numbers).
Behavioral insights: Frequency of communication, network patterns, or geospatial movement trends.
Together, these components form a rich data profile that organizations can leverage for various purposes phone number data from identity verification to targeted marketing.
Sources of Phone Number Data
Phone number data can originate from multiple sources:
Telecom Providers: Phone companies collect call logs, SMS activity, and data usage.
Apps and Websites: Many apps request users’ phone numbers for registration and may collect contact data and device information.
Public Records and Directories: Some databases aggregate public contact information from business listings, customer databases, or government records.
Data Brokers: Specialized firms compile phone number databases by scraping, purchasing, or licensing user data from various sources.
The way phone number data is collected and used depends significantly on regional privacy laws and user consent mechanisms.
Common Uses of Phone Number Data
1. Marketing and Customer Engagement
Businesses often use phone number data to run SMS marketing campaigns, personalized promotions, or customer support outreach. With platforms like WhatsApp Business, Viber, or SMS gateways, phone numbers become a direct channel to consumers.
Example: E-commerce companies may send cart reminders or shipping updates to users via SMS.
2. Authentication and Security
Phone numbers are a key part of multi-factor authentication (MFA). Services send verification codes via SMS or call to confirm a user's identity.
Use Cases:
Two-factor authentication (2FA)
Account recovery
Fraud detection via SIM swap detection
3. Lead Generation and Data Enrichment
Sales and marketing teams enrich existing leads by adding phone number data to contact records. Data providers offer reverse lookup tools to identify company roles, job titles, or social media profiles from a number.
4. Communication Analytics
Call centers and telecoms analyze phone number data to study patterns, optimize service delivery, and reduce call fraud or spam.
5. Government and Emergency Services
Authorities use phone data for contact tracing (e.g., during COVID-19), disaster alerts, and emergency location tracking. This data can also help law enforcement track criminal activity.
Phone Number Data in Business Intelligence
Phone numbers help businesses:
Map consumer journeys across channels
Create segmentation models based on call behavior
Track user response to campaigns
Monitor customer satisfaction in service departments
Modern CRMs (Customer Relationship Management systems) store not just the number but all associated interactions—calls, texts, and support tickets—to create a 360-degree view of each contact.
Risks and Concerns with Phone Number Data
Despite its usefulness, phone number data presents several risks, especially related to privacy and cybersecurity.
1. Privacy Invasion
Phone numbers are often linked to other personally identifiable information (PII). When shared without proper consent, it can result in privacy violations, spam, or harassment.
2. Phishing and Scam Calls
Fraudsters often spoof caller IDs or use leaked numbers to impersonate legitimate entities. This has led to a surge in robocalls, vishing (voice phishing), and SMS scams.
3. Data Breaches
Phone numbers are commonly leaked in data breaches, sometimes alongside passwords and personal data. Leaked phone data can be weaponized for identity theft or account hijacking.

Notable Incident: The 2019 Facebook data leak exposed phone numbers of over 500 million users, emphasizing the risks associated with poor phone data handling.
4. SIM Swapping
Hackers use phone number data to execute SIM swap attacks—porting a number to a new SIM to gain control of bank accounts, emails, and crypto wallets.
Legal and Regulatory Considerations
As data protection laws tighten globally, the handling of phone number data is under increased scrutiny.
GDPR (EU)
Considers phone numbers as personal data.
Requires explicit consent for collecting and processing.
Grants users the right to access, correct, or delete their data.
CCPA (California)
Gives consumers the right to opt out of phone data sales.
Requires companies to disclose what data is collected and why.
TRAI (India)
Imposes strict regulations on unsolicited commercial communication (UCC) to prevent spam.
Requires telemarketers to register and follow opt-in principles.
Organizations must implement proper data protection policies, encryption standards, and consent management practices to comply with these regulations.
Phone Number Data in the Age of AI and Automation
Artificial Intelligence (AI) and machine learning are transforming how phone number data is processed:
1. Predictive Analytics
AI models analyze call and message patterns to predict user behavior, identify churn risks, or target high-value customers.
2. Voice and Sentiment Analysis
AI can evaluate tone and emotion in voice calls to assess customer satisfaction or detect potential fraud.
3. Spam Detection
Machine learning algorithms detect spam calls and automatically block them based on number patterns and crowd-sourced data.
4. Virtual Assistants
Chatbots and voice bots use phone number data to authenticate users and personalize responses during interactions.
The Future of Phone Number Data
1. Decentralized Identity Systems
Blockchain and self-sovereign identity (SSI) systems may reduce reliance on centralized phone number databases, giving users more control over their identity and privacy.
2. eSIM and Number Portability
With the rise of eSIMs and number portability, users can change networks without changing their number. This increases the longevity of phone number data and its use as a long-term identifier.
3. Phone Numbers as Digital IDs
In many developing countries, phone numbers serve as digital IDs for banking, government services, and mobile payments. This trend is likely to expand as mobile-first economies grow.
4. Enhanced Consent and Transparency
Future data systems will likely include dashboards where users can see how their phone number data is used and revoke access in real-time.
Best Practices for Managing Phone Number Data
Organizations that collect and use phone number data should adhere to these best practices:
Obtain Explicit Consent: Always inform users why their number is needed and how it will be used.
Encrypt Data: Store numbers securely and ensure they are encrypted both at rest and in transit.
Implement Access Controls: Limit access to phone data to only those who need it.
Monitor for Breaches: Use tools to detect unauthorized access or data leaks.
Honor Opt-Out Requests: Make it easy for users to opt out of communications or data sharing
Thanks for reading..
SEO Expate Bangladesh Ltd.
0 notes
Text
As a deeply deeply anti-AI person and millennial luddite (I hate the fucking fact that fucking WhatsApp is on my phone and tumblr is the only social media I use), I agree. As much as I hate ai and I know that using it is going to evaporate so many skills that were normal for people to possess (googling, writing a fucking paragraph), I know that that's a feeling, not an argument. I can personally not use ai and live life, but if people don't want to possess the skill of writing and outsource that to ai there isn't a real reason for them not to. It's stupid to me, but it's the same logic as "we used to remember phone numbers in our head, now nobody knows numbers by heart" yes cause they don't have to. There's now a device that does that for you, and that's what technology is for.
Best best actual argument against ai which is not moral or ethical or philosophical is copyright law. If the multitude of cases pending in several different jurisdictions succeed then ai will lose its (perceived) right to scrape information from people who have created it. That would kneecap it.
However I have to admit I don't give a single tiny little fuck about copyright law, and from what I know of it, it's a little bitch. I am hitching my wagon manipulatively not to "ai bad for your brain" but to "ai illegal under copyright law".
You can't argue against a technology. No one has ever, ever, in the history of humanity, argued a technology out of existence. The closest we've come are nukes and human genetic engineering. Nukes exist and multiple countries have massive arsenals of them, but we've agreed not to use them because it would mean humanity's utter destruction. Human genetic engineering cuts right to the heart of a bunch of ethical questions about health, equality, identity, and so on, and also up until very recently genetic engineering has been a long and extremely expensive process. We'll see how long human genetic engineering remains taboo now that it's getting cheaper and easier. But these are absolute outliers. In the vast, vast majority of cases, I mean literally in virtually every single case, when people fight a new technology—for any reason—they loose.
There is no tenable "anti-AI art" position, just like there was never a tenable anti-loom position, or anti-railroad position, or anti-horseless carriage position. These things were doomed to fail absolutely from day one, as soon as the technology existed, and anti-AI art is doomed to fail just as utterly and completely. There is just no path here, if this is what you've hitched your wagon to I really do not know what to tell you.
4K notes
·
View notes
Text

Phone number crawler
In an increasingly connected world, businesses are constantly seeking innovative ways to engage with their audiences. WhatsApp, with its immense user base and user-friendly interface, has become a pivotal platform for communication. However, managing contacts can be a challenge, particularly when trying to expand your reach. This is where a WhatsApp number scraper comes into play, offering a powerful solution for businesses and marketers alike.
What is a WhatsApp Number Scraper?
A WhatsApp number scraper is a specialized tool designed to extract phone numbers from various sources, such as websites, social media, or other digital platforms. This enables users to compile a comprehensive list of contacts for outreach purposes. Unlike traditional methods of collecting numbers, a scraper automates the process, making it faster and more efficient.
Why Use a WhatsApp Number Scraper?
Efficient Contact ManagementOne of the primary benefits of using a WhatsApp number scraper is the efficiency it brings to contact management. Businesses often have large databases of potential clients, and manually collecting contact information can be incredibly time-consuming. A scraper allows you to gather numbers in bulk, streamlining your efforts significantly.
Targeted Marketing CampaignsEffective marketing relies heavily on reaching the right audience. With a WhatsApp number scraper, you can extract numbers that are relevant to your target demographic. This enables you to create focused marketing campaigns that resonate with specific groups, enhancing your overall outreach strategy.
Building a Stronger NetworkNetworking is essential for any business looking to grow. A number scraper helps you identify potential leads and collaborators by gathering contacts from relevant groups and discussions. By expanding your network, you can foster relationships that lead to valuable business opportunities.
How to Choose the Right WhatsApp Number Scraper
When selecting a WhatsApp number scraper, keep the following factors in mind:
Ease of UseOpt for a tool that features an intuitive interface. The easier it is to navigate, the more efficiently you can gather the numbers you need without a steep learning curve.
Source CompatibilityEnsure that the scraper can extract numbers from the sources you plan to target, whether that’s social media platforms, websites, or forums. Compatibility is key to maximizing your scraping efforts.
Data SecurityGiven that you’re dealing with personal contact information, prioritize scrapers that emphasize data security and comply with privacy regulations. Protecting the data you collect is crucial for maintaining trust with your audience.
Customer SupportLook for tools that offer reliable customer support. If you encounter issues or have questions, responsive support can help you navigate challenges and optimize your use of the tool.
Best Practices for Using a WhatsApp Number Scraper
Respect Privacy RegulationsWhen scraping numbers, it’s essential to be aware of privacy laws and regulations. Ensure that you have permission to contact individuals and respect their privacy to avoid potential legal issues.
Regular UpdatesTo maintain the quality of your contact list, consider using the scraper regularly. This helps you keep your database current and relevant, which is crucial for effective communication.
Organize Your DataOnce you’ve extracted the numbers, take time to organize them. Categorizing contacts based on interests, demographics, or other criteria can enhance your marketing efforts and improve engagement.
Conclusion
In the realm of digital marketing and communication, a WhatsApp number scraper can be an invaluable asset for businesses looking to expand their reach and connect with their audience. By automating the process of gathering contact information, a scraper not only saves time but also allows for more targeted and effective marketing strategies.
Whether you’re a small business owner, a marketer, or someone looking to grow your network, utilizing a WhatsApp number scraper can provide the edge you need to succeed. Embrace this powerful tool and watch as it transforms your communication strategies, enabling you to engage with your audience more effectively than ever before.
#WhatsApp contact extractor#WhatsApp number scraper#Global phone number downloader#Contact harvesting tool#International WhatsApp data extraction#Phone number scraper software#Worldwide contact finder#Global#phone directory scraper#WhatsApp data mining tool#International contact extraction
0 notes
Text
Sunset Marina & Celebration Party at Dhow Cruise
Introduction
Enjoy the Sunset Marina Dhow Cruise and find yourself in the enchanting atmosphere of Dubai evening at the fleet of Dhows on water. The Celebration Party at Dhow Cruise is a fitting for making your celebrations a memorable event! Marina becomes rather lively in the evening with lights of the city just reflected in the water and accompanied by lively music gives a magical touch.
Sunset Marina Dhow Cruise is not just merely a ride on a boat, this is an experience with a quite exquisite dinner cruise, chance to witness and capture beautiful views, and finally, partying on a wooden dhow. Whether it is a birthday, an engagement or just going out on a dinner date, the Sunset Marina Dhow Cruise holds a guarantee of a good time full of fun and beautiful sights on Dubai. Please contact on our whatsapp number to get more details or to book one for you.
Itinerary & Inclusions in Sunset Marina & Celebration Party at Dhow Cruise
The Sunset Marina Dhow Cruise provides an ultimate package because it aims at making all our customers happy.
Welcome Drinks: You are welcomed by different options of welcome drinks on arrival and feel quite relaxed and prepared for the nice evening.
Buffet Dinner: Feast on an elaborate complimentary International buffet dinner including Arabic dishes. Special attention is paid to the menu which includes dishes for every taste and any diet.
Live Entertainment: The cruise also offers entertainment in form of dances and music from the cultures of the respective countries.
Celebration Party: The main focus of the day, loaded with a DJ and lights, changes into a dancing area that is ideal to enjoy the selected occasions.
Scenic Views: Angled along the beautiful Dubai Marina and you are likely to catch a glimpse of beautiful sky scrapes exciting tourist attractions as you cruise.
Comfortable Seating: There will be good sitting arrangements so that it is comfortable and the you enjoy the cruise.
Note: An experienced and well-mannered crew is always there to meet every need of customers to ensure they have an excellent time. And we take pride in providing the best services! So, call us for booking Sunset Marina Dhow Cruise now.
Highlights of Sunset Marina & Celebration Party at Dhow Cruise
Stunning Sunset Views: Watch the beautiful sunset on the Marina with the entire sky painted in shades of orange and pink, the perfect picture for those cameras.
Dhow Ambiance: The wooden boat, dhow, and decoration with lights and necessary items give a very royal and traditional appearance.
Cultural Performances: The Arab live dance performances add value to the cultural aspect and include the splendid spinning dance known as Tanoura dance.
Delicious Cuisine: The extravagant dinner menu is offered on a buffet basis, which guarantees all of your satisfaction in terms of food choice.
Lively Celebration Party: The fantastic night will be spent dancing on the open deck with live music and illumination when the dhow turns into a floating disco.
Iconic Landmarks: The boat will cruise some of the major attractions of the city in Dubai such as the Burj Al Arab and Atlantis Hotel, thus enabling you get good shots of other Dubai attractions.
Starry Night Sky: During night, you get to enjoy the starry night sky which makes the evening magical as it continues to get darker.
Important Information about Sunset Marina Dhow Cruise
Timings: The cruise is usually taken in the evening, it can be from 7:00 PM and may take about two to three hours. Be sure to check the actual hours while booking your Celebration Party at Dhow Cruise
Dress Code: Business casual wear would be appropriate. Shoes should be comfortable shoes as you might be going to dance, especially for a long time,.
Booking: Booking of a slot should be done in advance, especially for weekends and special occasion so as to fill in for the slot.
Location: This makes the boarding point to be at Dubai Marina. The specific location details will be given in the bookings details.
Inclusions: The cost of the package is restricted to welcome drinks, buffet dinner and live entertainment as well as entry on-board.
Accessibility: The dhow is very much able to meet the requirements of anyone that may have mobility problems.
Weather Conditions: The cruise is able to function, or is open, in nearly all sorts of weather. Nevertheless, in the situations of extreme conditions, it can be changed or stopped with the refunds.
Book Sunset Marina Dhow Cruise
Try the Sunset Marina Dhow Cruise and start creating perfect moments of fun, fun and celebration. Whether you are going out on a date or any form of special event or celebration, this is among the things that you should not miss as you tour Dubai. Call us to get your trip on water fixed!
0 notes
Text
VeryUtils Google Maps Scraper is a scraping tool for business leads to extract data from Google Maps and export to CSV/JSON/EXCEL file
VeryUtils Google Maps Scraper is a scraping tool for business leads to extract data from Google Maps and export to CSV/JSON/EXCEL file, includes reviews, images, phone number, email address and social media profiles.
In the fast-paced world of business, having access to accurate and up-to-date information is crucial for success. Whether you're a marketer looking to reach new clients, a sales professional aiming to expand your customer base, or a business owner seeking to stay ahead of the competition, the ability to gather valuable leads efficiently can make all the difference. Enter VeryUtils Google Maps Scraper, a powerful tool designed to revolutionize the way you extract business data from Google Maps.

What is Google Maps Scraper?
Google Maps Scraper is a cutting-edge solution for capturing business leads and extracting data from Google Maps with unparalleled ease. With just a single click, you can retrieve a wealth of information, including business names, addresses, photos, coordinates, websites, emails, phone numbers, social media profiles, and more. This data can then be exported to CSV, JSON, Excel, or other file formats, allowing for seamless integration with your existing tools and workflows.
Google Maps Scraper Key Features:
Let's delve into some of the key features that make VeryUtils Google Maps Scraper a must-have tool for businesses of all sizes:
Efficient Data Extraction: Quickly search and extract business information from Google Maps, saving valuable time and effort.
Comprehensive Lead Generation: Gather leads including website URLs, email addresses, and social media profiles to build a robust database of potential customers.
Flexible Export Options: Export data to Excel or CSV files for easy analysis and integration with other marketing and CRM tools.
Streamlined Workflow: Simplify lead generation processes and enhance productivity across your marketing, sales, and outreach teams.
Who Can Benefit?
VeryUtils Google Maps Scraper is designed to cater to a wide range of users, including:
B2B Marketers: Find quality email addresses and essential features to attract your next major client.
SaaS Companies: Enhance your outreach teams' effectiveness in expanding and retaining your customer base.
Sales Teams: Utilize our comprehensive tool suite to reach a larger customer base and close more deals.
Growth Hackers: Achieve accurate and efficient user base growth without dedicating all your time to outreach efforts.
Conclusion
In conclusion, VeryUtils Google Maps Scraper is more than just a tool – it's a game-changer for businesses looking to stay ahead in today's competitive landscape. With its advanced features, user-friendly interface, and unparalleled efficiency, it's your ultimate solution for lead generation and business growth. Whether you're a seasoned marketer or a budding entrepreneur, make VeryUtils Google Maps Scraper your go-to tool for unlocking new opportunities and driving success. Try it today and experience the difference for yourself!
0 notes
Text
Meta Exposes Eight Firms Behind Spyware Attacks on iOS, Android, and Windows Devices
Meta Platforms’ Actions Against Surveillance-for-Hire Companies
Meta Platforms has taken action against eight surveillance-for-hire companies based in Italy, Spain, and the United Arab Emirates (U.A.E.), as per their Adversarial Threat Report for Q4 2023. The companies were reportedly involved in malicious activities, including the development of spyware aimed at iOS, Android, and Windows devices.
The malware developed by these companies had the ability to gather and access a wide range of device data, including information about the device itself, location data, photos, media, contacts, calendar entries, emails, SMS, and data from social media and messaging apps. The malware could also activate device microphones, cameras, and screenshot functions.
The companies implicated in these activities are Cy4Gate/ELT Group, RCS Labs, IPS Intelligence, Variston IT, TrueL IT, Protect Electronic Systems, Negg Group, and Mollitiam Industries. According to Meta Platforms, these companies also engaged in data scraping, social engineering, and phishing activities across a variety of platforms, including Facebook, Instagram, X (formerly Twitter), YouTube, Skype, GitHub, Reddit, Google, LinkedIn, Quora, Tumblr, VK, Flickr, TikTok, SnapChat, Gettr, Viber, Twitch, and Telegram.
Specific Malicious Activities
RCS Labs, owned by Cy4Gate, reportedly used a network of fake personas to trick users into providing their phone numbers and email addresses, and to click on fraudulent links for reconnaissance purposes. Facebook and Instagram accounts linked to Spanish spyware company Variston IT were used for exploit development and testing, including the sharing of malicious links. Reports suggest that Variston IT is in the process of shutting down its operations.
Meta Platforms also identified accounts used by Negg Group for testing spyware delivery, and by Mollitiam Industries, a Spanish company offering data collection services and spyware for Windows, macOS, and Android, for scraping public information.
Actions Against Coordinated Inauthentic Behavior (CIB)
Alongside these actions, Meta Platforms also removed over 2,000 accounts, Pages, and Groups from Facebook and Instagram due to Coordinated Inauthentic Behavior (CIB) originating from China, Myanmar, and Ukraine. The Chinese cluster targeted U.S. audiences with content criticizing U.S. foreign policy towards Taiwan and Israel and supporting Ukraine. The Myanmar network targeted local residents with articles praising the Burmese army and criticizing ethnic armed organizations and minority groups. The Ukrainian cluster used fake Pages and Groups to post content supporting Ukrainian politician Viktor Razvadovskyi and expressing support for the current government and criticism of the opposition in Kazakhstan.
Industry-wide Efforts to Curb Spyware Abuse
This action by Meta Platforms comes as part of a broader initiative involving a coalition of government and tech companies aiming to curb the abuse of commercial spyware for human rights abuses. As part of its countermeasures, Meta Platforms has introduced new features such as Control Flow Integrity (CFI) on Messenger for Android and VoIP memory isolation for WhatsApp to make exploitation more difficult and reduce the overall attack surface.
The Persistence of the Surveillance Industry
Despite these efforts, the surveillance industry continues to evolve and thrive in various forms. Last month, 404 Media, building on prior research from the Irish Council for Civil Liberties (ICCL) in November 2023, revealed a surveillance tool called Patternz. This tool utilizes real-time bidding (RTB) advertising data from popular apps like 9gag, Truecaller, and Kik to track mobile devices. The Israeli company behind Patternz, ISA, claims that the tool allows national security agencies to use real-time and historical user advertising data to detect, monitor, and predict user actions, security threats, and anomalies based on user behavior, location patterns, and mobile usage characteristics.
In addition, last week, Enea unveiled a previously unknown mobile network attack known as MMS Fingerprint.
The Use of Pegasus-maker NSO Group’s Alleged Techniques
According to some sources, the Pegasus-maker NSO Group is believed to have employed specific techniques, as stated in a contract they had with Ghana’s telecom regulator in 2015. The exact means used by the group are still somewhat unclear. However, Enea, a Swedish telecom security firm, has put forward a plausible theory.
The Role of Binary SMS in the Suspected Method
Enea suggests that the group likely used a unique form of SMS message known as binary SMS, specifically MM1_notification.REQ. This particular message informs the recipient’s device of an MMS (Multimedia Messaging Service) that is pending retrieval from the MMSC (Multimedia Messaging Service Center).
The Process of Fetching MMS
The process of fetching the MMS involves the utilization of MM1_retrieve.REQ and MM1_retrieve.RES. The former is an HTTP GET request directed to the URL address contained in the MM1_notification.REQ message.
The Significance of User Device Information
What makes this technique particularly interesting is the inclusion of user device information such as User-Agent (distinct from a web browser User-Agent string) and x-wap-profile in the GET request. This data essentially serves as a unique identifier for the device.
Understanding User-Agent and X-wap-profile
Enea explains that the User-Agent in this context is a string that typically identifies the device’s OS and model. The x-wap-profile, on the other hand, points to a User Agent Profile (UAProf) file that outlines the capabilities of a mobile handset.
Potential Exploitation of Device Information
This device information could potentially be used by a threat actor to deploy spyware. They could exploit specific vulnerabilities, customize their harmful payloads to suit the target device, or even design more efficient phishing campaigns. However, it’s important to note that there is currently no evidence to suggest this security loophole has been exploited in recent times.
https://www.infradapt.com/news/meta-exposes-eight-firms-behind-spyware-attacks-on-ios-android-and-windows-devices/
0 notes
Text
How to Choose a WhatsApp Number Information Scraping Software?
With the rise of WhatsApp marketing, there has been an increasing number of related auxiliary software available in the market. Many marketers often find themselves struggling to choose the right marketing software for their needs, which is a major source of frustration. Today, we will explain what factors you should consider when selecting the right marketing auxiliary software for yourself.

Using the example of selecting scrape WhatsApp numbers software, we will discuss the important aspects to consider when choosing auxiliary software:
First, we need to check and understand the actual core features of the software. Many marketing software titles do not align with their actual functions. To avoid this, we should either download the software to test it ourselves or look at reviews from others online. For example, with scrape WhatsApp numbers software, some vendors focus more on mass messaging and account maintenance, with the data scraping feature being a secondary focus. This might not fully meet our needs.
Next, we should examine the software’s operating mode to determine whether the process is complicated and whether it allows for custom options in multiple areas. Taking CrownSoft's scrape WhatsApp numbers software as an example, the software is very easy to use. We simply import our phone numbers, log into the WhatsApp account used for data scraping, and quickly complete the scraping operation. Additionally, we can manually adjust the depth of information to be scraped, such as recognizing age, gender, and signature language based on the avatar and signature.
Finally, we need to consider the after-sales service and maintenance of the software. WhatsApp updates frequently, and if the software is not properly maintained and updated, it could pose security risks to our marketing efforts and accounts. Therefore, it is crucial to avoid these situations by choosing auxiliary software that is regularly maintained and updated.
That concludes the content about “How to choose scrape WhatsApp numbers software?”. We are honored that you found and read this article, and we sincerely thank you! If you have any questions or need further information about this article, feel free to contact us.
CrownSoft's scrape WhatsApp numbers software allows you to choose multiple methods to generate phone numbers for different regions. By logging into your account, the software will analyze and display whether the WhatsApp account is registered. It uses CrownSoft’s proprietary program to filter account information more precisely, including avatar, age (auto-recognition), gender (auto-recognition), signature, and signature language (auto-recognition). The filtered data can be exported in .txt, .xls, .xlsx, or .vcf formats.
#CrownSoft's scrape WhatsApp numbers software#scrape WhatsApp numbers software#scrape WhatsApp numbers#whatsapp marketing#whatsapp
0 notes
Text
On Personal InfoSec
Been awhile since I've had one of these posts but I figure with all that's going on in the world it's time to make another one of these posts and get some stuff out there for people. A lot of the information I'm going to go over you can find here:
So if you'd like to just click the link and ignore the rest of the post that's fine, I strongly recommend checking out the Privacy Guides.
Browsers:
There's a number to go with but for this post going forward I'm going to recommend Firefox. I know that the Privacy Guides lists Brave and Safari as possible options but Brave is Chrome based now and Safari has ties to Apple. Mullvad is also an option but that's for your more experienced users so I'll leave that up to them to work out.
Browser Extensions:
uBlock Origin: content blocker that blocks ads, trackers, and fingerprinting scripts. Notable for being the only ad blocker that still works on Youtube.
Privacy Badger: Content blocker that specifically blocks trackers and fingerprinting scripts. This one will catch things that uBlock doesn't catch but does not work for ads.
Facebook Container: "but I don't have facebook" you might say. Doesn't matter, Meta/Facebook still has trackers out there in EVERYTHING and this containerizes them off away from everything else.
Bitwarden: Password vaulting software, don't trust the password saving features of your browsers, this has multiple layers of security to prevent your passwords from being stolen.
ClearURLs: Allows you to copy and paste URL's without any trackers attached to them.
VPN:
Note: VPN software doesn't make you anonymous, no matter what your favorite youtuber tells you, but it does make it harder for your data to be tracked and it makes it less open for whatever network you're presently connected to.
Mozilla VPN: If you get the annual subscription it's ~$60/year and it comes with an extension that you can install into Firefox.
Proton VPN: Has easily the most amount of countries serviced, can take cash payments, and does offer port forwarding.
Email Provider:
Note: By now you've probably realized that Gmail, Outlook, and basically all of the major "free" e-mail service providers are scraping your e-mail data to use for ad data. There are more secure services that can get you away from that but if you'd like the same storage levels you have on Gmail/Outlook.com you'll need to pay.
Proton Mail: Secure, end-to-end encrypted, and fairly easy to setup and use. Offers a free option up to 1gb
Tuta: Secure, end-to-end encrypted, been around a very long time, and offers a free option up to 1gb.
Email Client:
Thunderbird if you're on Windows or Linux
Apple Mail if you're on macOS
Cloud Storage:
Proton Drive: Encrypted cloud storage from the same people as Proton Mail.
Tresorit: Encrypted cloud storage owned by the national postal service of Switzerland. Received MULTIPLE awards for their security stats.
Peergos: decentralized and open-source, allows for you to set up your own cloud storage, but will require a certain level of expertise.
Microsoft Office Replacements:
LibreOffice: free and open-source, updates regularly, and has the majority of the same functions as base level Microsoft Office.
OnlyOffice: cloud-based, free, and open source.
Chat Clients:
Note: As you've heard SMS and even WhatsApp and some other popular chat clients are basically open season right now. These are a couple of options to replace those.
Signal: Provides IM and calling securely and encrypted, has multiple layers of data hardening to prevent intrusion and exfil of data.
Molly (Android OS only): Alternative client to Signal. Routes communications through the TOR Network.
Briar: Encrypted IM client that connects to other clients through the TOR Network, can also chat via wifi or bluetooth.
Now for the last bit, I know that the majority of people are on Windows or macOS, but if you can get on Linux I would strongly recommend it. pop_OS, Ubuntu, and Mint are super easy distros to use and install. They all have very easy to follow instructions on how to install them on your PC and if you'd like to just test them out all you need is a thumb drive to boot off of to run in demo mode.
If you game through Steam their Proton emulator in compatibility mode works wonders, I'm presently playing a major studio game that released in 2024 with no Linux support on it and once I got my drivers installed it's looked great. There are some learning curves to get around, but the benefit of the Linux community is that there's always people out there willing to help.
I hope some of this information helps you and look out for yourself, it's starting to look scarier than normal out there.

#information security#infosec#computer security#computer infosec#personal infosec#browsers#internet browser#email#instant messaging#cloud storage#linux#pop os#linux mint#ubuntu#firefox#firefox extensions#long post
67 notes
·
View notes
Note
zhouvries + mick
Buzz. Buzz buzz buzz. Buzz.
Mick groans, pulling his head out from under the covers, the cool air of the bedroom hitting him in the face. He fumbled around on the bedside table for a moment, nearly knocking over his glass of water, before grabbing his phone. It makes a satisfying dull thump when it, miraculously, lands on the pile of Mick’s clothes he had left on the floor last night.
He is too tired to care.
The bathroom door opens, the room filling with steam and the heated smell of shampoo and body wash. Mick inhales, throwing an arm over his face.
Lewis laughs, footsteps soft on the carpet, and the bed dips, a solid weight settling over Mick’s knees. “It’s not even eight, how can anyone have pissed you off this much?”
Mick lifts his arm a little, narrowing his eyes into a glare. “I was woken up and it’s not even eight.”
Lewis’s face creases into a smile, shower flushed cheeks bunching. He’s dried himself off already, he wouldn’t have gotten on the bed if he hadn’t, the freak, but his neck is still damp, shoulders shining faintly. The lashes on his left eye are clumped together, dark and stark against the thin skin of his eyelid. Mick reaches out a finger to press into the skin there.
Lewis sways back, face like a disgruntled cat. Right. Mick rolls his eyes, smiling. He’s just done his skincare. Needs a minute before the products have sunk in properly.
Lewis lets him pull him in for a kiss though, not caring about Mick’s morning breath. It’s open mouthed and wet and warm and a little gross and almost makes up for Mick waking up an hour earlier than he had intended.
“You didn’t mind me waking you up a few hours ago. Before I went on my run.” Lewis leans in closer, shifting his weight, and drags a hand through Mick’s hair, nails scraping behind his ear.
Mick raises his eyebrows. “Yeah.” He presses his mouth against the corner of Lewis’s, where the skin folds into soft long laugh lines. His body aches faintly from last night, his lower back pulling from when Lewis fucked into him, nice and slow and rolling. If he wasn’t still loose from that, he would be from waking up to Lewis gently pushing him over onto his stomach so he can lick and eat him open, the sun barely risen, Mick, hazy with sleep and pleasure and the quiet almost hurt sounds Lewis was making.
“Somehow I didn’t mind that as much.”
Lewis laughs again, nose brushing Mick’s before pulling away, lying out flat on him, arms crossed over Mick’s chest, chin resting on them. He reached up one hand to tap Mick’s cheek with the phone Mick had thrown earlier.
“Could be important.”
Mick scoffs. “I doubt it.”
He takes the phone from him, holding it up to his face, squinting against the harsh brightness. There are nine notifications waiting for him in the 🍼🍼🍼🥤🥤🥤 Whatsapp group chat. The little red number rises as Mick debates blocking them all.
A notification pops up at the top of the screen.
Nyck: guys pls be serious i’ve fucked up here
And another one.
Sean: fucked UP is for sure
Arthur: yuh guanyu is sooooo out of ur league
Nyck: MICK HELP
Nyck: I CAN SEE UR LITTLE LIGHT IS ON. IT SAYS UR ONLINE
Nyck: @MickSchumacher !!!!!!!!!!
Mick sighs, scooching his ass down in the bed until Lewis is sitting properly on his hips, face closer. Lewis watches him, amused.
Mick runs a hand over his hair, tracing the shape of Lewis’s ear. He tilts his chin up. “Another.”
Lewis grins and pushes himself up to kiss him. Mick melts into it, pulling Lewis in closer, and spreads his legs wider. Lewis rolls his hips slightly and laughs. The thin silk sheets do nothing to hide the way Mick is already half hard.
“Really? Again?”
Mick shrugs, shameless, and lets his knees fall open. Lewis plants his hands on either side of Mick’s head to steady himself.
“What — are you sixteen or something?”
Mick laughs, turning his cheek to press a kiss into the inside of Lewis’s wrist. “Man, if sixteen year old me was faced with you coming out of our shower, only in a towel, he’d have ruined these sheets already.”
Lewis’s eyes are all blurry up this close but he looks pleased. The weirdo.
“You say the sweetest things to me,” Lewis murmurs, shifting, exhaling into a laugh as Mick groans. Lewis’s hand is warm and heavy, his palm pressing down over the sheet.
Buzz. Buzzzzz. Buzz. Buzz.
“It’s like they want to die.”
Mick lifts his head only to let it thump back onto the bed. Lewis’s breathing hitches, wheezing as he dissolves into giggles, shuffling over until he’s lying on his side next to Mick, cheek propped up on his hand.
Mick looks up at the ceiling, mourning the morning he could’ve had, and grabs at his phone beside him.
Nyck: mick i am going to commit. none of the guys are being helpful
Marcus: wdym!!!!!!!!!! we are the most helpful
Sean: yeah bruv
Nyck: BRUV???? YOURE NOT EVEN ENGLISH
Sean: hey. i watch love island
Mick: Someone better be bleeding. I was having a good morning
Nyck: thank FUCK
Arthur: read: i was sucking lewis dick and it was sloppy
Marcus: or he was getting railed. we don’t know his life. we don’t know his story
Mick coughs, choking on spit, and tries to angle the phone away from Lewis, who only cackles, elbows digging into Mick's ribs.
Arthur: railed. question mark
Sean: he means getting fucked. like. dick in ass
Arthur: oh
Arthur: wait
Arthur: @MickSchumacher
Arthur: r u telling me that u have the sir lewis hamilton in ur bed n ur NOT tapping that ass. question mark. question mark
"Yeah, Mick," Lewis says, delighted. "Why aren't you tapping my ass?" He presses his mouth into the muscle of Mick's shoulder, not even bothering to hide his smile.
"I literally fucked you yesterday morning," Mick replies dryly.
Sean: retweet
Nyck: i second that retweet
Marcus: how do u know tapping that ass but not railed
Callum: none of these words are in the bible
Callum: also
Callum: arthur pls don't tell me you said 'question mark' bc you forgot where the ? is on your keyboard again
Arthur: listen
Sean: BRUV
Arthur: IT IS HARD BEING PRETTY
Arthur: Y DO U WANT ME TO BE SMART 2
Marcus: ur not a real person
"What's with the emojis?" Lewis asks, pointing at the top of the screen. Mick grimaces and then says, "It was Sean's idea. They're milk bottles and you know, a takeaway cup. For - milkshakes. Because, you know." He hums the tune of my milkshake brings all the boys to the yard, shoving at Lewis when he laughs.
“Aw, man. That’s precious.”
Mick rolls his eyes.
Mick: I am leaving this gc I can't deal
Nyck: NO WAIT I NEED YOUR HELP
Nyck: i accidentally told guanyu that i wanted to see his dick and like. mb suck it and have his babies and do a spring wedding bc he’d look so pretty surrounded by cherry blossoms and mb get a cat. and then ran away
Lewis rubs his knuckles into his sternum as he lies flat on his back, trying to breathe around his laughter. Mick shakes his head.
Sean: BRUV
Callum: how do you ACCIDENTALLY say that
Marcus: yeah mate that's a whole fucking monologue
Nyck: HE WAS IN A CROP TOP I WAS V OVERWHELMED OKAY THERE WAS A LOT GOING ON
Nyck: i am only so strong
Callum: clearly
Nyck: he was also wearing lipgloss
Sean: understandable
Arthur: now i want a baby. do u think id be a good dad
Mick: THIS IS WHAT YOU WOKE ME UP FOR??
Nyck: i am so unloved here
#this is so unbelievably stupid . the exams are rotting my brain fr#schumilton#ft. The Lads#this is barely even zhouvries im sorry#flash fic#kyle tag#niamh.asks
25 notes
·
View notes
Text

Global phone number downloader
In an increasingly connected world, businesses are constantly seeking innovative ways to engage with their audiences. WhatsApp, with its immense user base and user-friendly interface, has become a pivotal platform for communication. However, managing contacts can be a challenge, particularly when trying to expand your reach. This is where a WhatsApp number scraper comes into play, offering a powerful solution for businesses and marketers alike.
What is a WhatsApp Number Scraper?
A WhatsApp number scraper is a specialized tool designed to extract phone numbers from various sources, such as websites, social media, or other digital platforms. This enables users to compile a comprehensive list of contacts for outreach purposes. Unlike traditional methods of collecting numbers, a scraper automates the process, making it faster and more efficient.
Why Use a WhatsApp Number Scraper?
Efficient Contact ManagementOne of the primary benefits of using a WhatsApp number scraper is the efficiency it brings to contact management. Businesses often have large databases of potential clients, and manually collecting contact information can be incredibly time-consuming. A scraper allows you to gather numbers in bulk, streamlining your efforts significantly.
Targeted Marketing CampaignsEffective marketing relies heavily on reaching the right audience. With a WhatsApp number scraper, you can extract numbers that are relevant to your target demographic. This enables you to create focused marketing campaigns that resonate with specific groups, enhancing your overall outreach strategy.
Building a Stronger NetworkNetworking is essential for any business looking to grow. A number scraper helps you identify potential leads and collaborators by gathering contacts from relevant groups and discussions. By expanding your network, you can foster relationships that lead to valuable business opportunities.
How to Choose the Right WhatsApp Number Scraper
When selecting a WhatsApp number scraper, keep the following factors in mind:
Ease of UseOpt for a tool that features an intuitive interface. The easier it is to navigate, the more efficiently you can gather the numbers you need without a steep learning curve.
Source CompatibilityEnsure that the scraper can extract numbers from the sources you plan to target, whether that’s social media platforms, websites, or forums. Compatibility is key to maximizing your scraping efforts.
Data SecurityGiven that you’re dealing with personal contact information, prioritize scrapers that emphasize data security and comply with privacy regulations. Protecting the data you collect is crucial for maintaining trust with your audience.
Customer SupportLook for tools that offer reliable customer support. If you encounter issues or have questions, responsive support can help you navigate challenges and optimize your use of the tool.
Best Practices for Using a WhatsApp Number Scraper
Respect Privacy RegulationsWhen scraping numbers, it’s essential to be aware of privacy laws and regulations. Ensure that you have permission to contact individuals and respect their privacy to avoid potential legal issues.
Regular UpdatesTo maintain the quality of your contact list, consider using the scraper regularly. This helps you keep your database current and relevant, which is crucial for effective communication.
Organize Your DataOnce you’ve extracted the numbers, take time to organize them. Categorizing contacts based on interests, demographics, or other criteria can enhance your marketing efforts and improve engagement.
Conclusion
In the realm of digital marketing and communication, a WhatsApp number scraper can be an invaluable asset for businesses looking to expand their reach and connect with their audience. By automating the process of gathering contact information, a scraper not only saves time but also allows for more targeted and effective marketing strategies.
Whether you’re a small business owner, a marketer, or someone looking to grow your network, utilizing a WhatsApp number scraper can provide the edge you need to succeed. Embrace this powerful tool and watch as it transforms your communication strategies, enabling you to engage with your audience more effectively than ever before.
#WhatsApp contact extractor#WhatsApp number scraper#Global phone number downloader#Contact harvesting tool#International WhatsApp data extraction#Phone number scraper software#Worldwide contact finder#Global#phone directory scraper#WhatsApp data mining tool#International contact extraction
0 notes
Note
Not dream anon but did have these 2 crazy dreams I'd like to share.
Dream 1 - so on my dream Fran had previously dated another player, I think she's in the championship and in a preseason game there was thing where she tried to tackle Fran but they end up tangled up together on the floor. The ref doesn't give a foul so Fran playfully gives her a nibble on the leg and the player gives Fran a smack on the bum. This blows up all over the media and internet like a controversial topic but try and calm it down the player releases screenshots of messages to show they're friends, but she forgets to crop out the part where they're dating so theres this message from Fran which says come give me cuddles and we'll watch 'cultured anime'. And that really blows up and is like the leading story on the news so Fran has to give a press conference explaining her tastes and defending all forms of Japanese art. Then I woke up.
Dream 2 - I'm walking down the riverside and pass by Naomi and baby 🐐. So I ask them for a selfie and then after they take it, Jessie asks for my number so that I can WhatsApp the pictures to her because she thinks they're cute. So we start messaging and eventually start dating 🥺 we get to the meet the parents stage but on top of me meeting her mum and dad I also have to seperately meet m&p, Maren, Melly, Aniek and Niamh, and then Emma to get all their approval. I somehow manage to scrape by and we eventually get married and have 3 children. She wins the balon d'Or one year and captains Canada to the world cup the next. When she retired she spends 15 years working on projects that eventually save the earth and after that she becomes canwnt manager and lets me be her assistant and together we win the Olympics and world cup. And even when we are together in our 80s shes still so baby faced that if it wasn't for the grey hair you'd guess she was late 30s
these were wiiiild, thanks for sharing
I don't even know what to say about the first one, every part of it was so crazy 😅 but awww the jflem dream is so wholesome 🥺 very believable too
3 notes
·
View notes
Link
Facebook, as well as WhatsApp and Instagram, have been gone from the internet for hours.
Internet users, clearly, are freaking out. Facebook has stated very little about what is actually taking place, however the outage is at the moment seemingly affecting only Facebook and its services. Many experts believe it to be associated to issues with internet infrastructure, particularly DNS and BGP.
Short for for Domain Name System, the DNS is a service that permits the internet to run by translating domains such as Facebook.com into IP addresses and vice versa. For some unknown reason, Facebook’s DNS records, in addition to BGP records, are gone from the internet. BGP (Border Gateway Protocol) is the system that figures out the best route for a packet to travel across the internet.
In this information vacuum, however, conspiracy theorists have begun speculating that this can be a massive hack, that it’s tied to Sunday evening’s “60 Minutes” episode during which a Facebook whistleblower said that Facebook is intentionally misleading the public and the federal government on its efforts to curb hate speech and misinformation, or is otherwise related to Facebook’s current problems in the news.
A music studio recording business posted a screenshot of what look to be a bunch of DNS addresses on Twitter and speculated that Facebook is gone forever, which quickly went viral with literally no context by any means. The screenshot appears to be stolen from one other Twitter account known as KillFearNY, which describes itself as a creative and sports agency.
Probably the most popular theories has centered around a supposed hack that resulted in 1.5 billion Facebook records being sold on a hacking forum. In this version, individuals are pointing to a September 22 post from a supposed company referred to as X2Emails which has “more than 1.5b Database of Facebook these database scraped this year and 100% emails are included and phone as well” and is somehow linked to today’s outage.
This theory does not even pass the smell test, though. The person who posted the advertisement does not even pretend the info was stolen from Facebook. The post says it was “scraped,” and it only contains: “We only have these fields : Emails , Gender , Location , cities , dob , phone numbers , names , uid.” Scraped databases of Facebook users show up on a regular basis and have little or nothing to do with any kind of hack.
What’s worse—or better depending on your viewpoint—is that it is very likely that this is all a scam anyway.
One other user in the forum thread alerted others to not trust the seller.
“Scammer. Only sends [a sample of] 20 users. There isn’t any more. Doesn’t accept escrow(moderator). However he expects you to believe in 20 samples and send $5,000. Instead of 1.5 billion, I believe there are 150 users of data for social engineering. “
Aric Toler, a researcher at Bellingcat, was one of the first ones to report that folks needs to be cautious and never take this at face value.
The fact that some wannabe hacker advertises scraped data on a hacking forum that anybody can access is nothing new. It occurs every other week. Typically, hackers who post on Raid Forums do have actual hacked data, however generally they’re simply attempting to rip-off other users.
Even other forum users aren’t taking it seriously.
“Hahahaha 600 TB of Mark Zucker burger selfies :D,” one person posted in a chat.
Facebook couldn’t be reached for comment due to the outage, which nonetheless has seemingly brought about mass chaos not just online but offline, too. Reporters at the New York Times, for instance, have noted that Facebook employees have been unable to get into certain buildings. Facebook employees have additionally had to talk with each other using secondary messaging services like Discord and Zoom.
In January of this year, Motherboard reported on a real incident where attackers scraped Facebook, obtaining a database of 500 million accounts. That database included phone numbers of people that actively tried to keep that data personal. Two months later somebody dumped the database on a hacking forum, according to reports at the time.
We’re still unsure what’s happening at Facebook, and an outage of this severity and length is unprecedented in Facebook history. There could very well be a very interesting explanation for the outage, however we simply do not know enough to say what caused it yet. One thing we’ve learned, though, is that conspiracy theories can spread across the internet just fine without Facebook.
15 notes
·
View notes
Text

oh GOD guys…. You have no idea the crusade i had to went through just to be sitting here, with my dear computer working again, and enjoying the joy of 1.9 Mbps internet connection speed. First thing on the front page of my dash was three shitposts on a row, new niche memes, and good ‘ol fandom drama. god how I missed this hell site.
In case anyone wants to know what happened, I will put behind a ‘read more’ the story of a missing computer part that quickly become a detective mission, that dragged me unwillingly into the wild ride I didn’t signed for when pressing ‘buy’ on an online store.
TL;DR at the end bc this is very long. English is not my first language so please bear with me!
Okay, some of you may know a bit about me since apparently i don’t have a “dude shut up! Stop oversharing your woes!!!” button on me but hey here are some things to know about me in case you are curious: I live in Venezuela and not having internet is my personality trait, living in my country is very hard, hard like trying to play the Rainbow Road of Mario Kart but you have butter on your hands, your eyes are closed and you are running on the rain while there is a 8.0 earthquake happening. That hard. I work as a freelance graphic designer and make art commissions so me and my family can survive the economic crisis on my country, having internet and a working computer is a really big deal, like literally we eat thanks to it. Now you see how that would led me to spend a whole month chasing and stressing over a stupid part my computer needed.
Back in December, remember last season of “what’s troubling Sirene now?” where i spend almost a month without internet and then yay internet is back! for like two days? well, after Christmas there was a sudden power cut one night and i was on my computer working on a commission but since this is now a common occurrence i didn't think anything of it …until next day when i tried to switch my computer ON it didn't. I tried everything to revive it, grabbing anxiously my hair, walking on circles, and pressing continuously the power button, you know everything, but it was in vain. It’s dead, Jim. As you can imagine i had a breakdown when i realized i won’t be able to work anymore and needed to buy a new power supply since this one was toast…and was without internet friggin again. AGAIN. I survived till now using my crappy phone data but heavy apps hardly load, tumblr/ao3/twitter sometimes loaded if i refreshed them like a madman.
My computer is a tiny model and has a power supply that apparently is made by beavers in Narnia, because is so uncommon that the only stores that sell them are on my Capital city two states away from where i live. Knowing this, there is not other alternative for me but to use a online store and shipping the package here, in theory sounds simple right? a reminder that this is a third world country, where everything is falling apart and barely holding it together with chewing gum and prayers, what are the odds of something going wrong hmm….
Okay, this happened in the week after Christmas and before New Year's Eve, so of course all stores in my country decided to go on vacation and return on January. I impatiently waited for two online stores to be back on business that have the power supply i need, they were physical stores too so i thought i would be safe. i liked one more than the other and, as i told my friends, i felt like a telenovela protagonist that was on a love triangle with two galanes but the hotter one was in coma and the other just had 3 episodes in, meaning that the better rated store was still offline and the other was online but only had like 3 products sold …not very reassuring but i desperately needed to start working again so i went with that one. Big mistake.
Everything started on Tuesday, January 14.
Mercado Libre is a page where people sell things like Amazon, this is where the seller of the power supply was, after you click on buy, you can see the seller info and a chat to talk to them, i wrote but there was not immediate response so i called, i spoke to a woman and she told me to text her on WhatsApp, that should have been my first red flag, if the app had a perfect chat option there why text outside of it??
whatever, i went and text her, asked when would she send the package and she told me “tomorrow” the shipping company she was going to use is called “Zoom” (remember that name bc it will be mentioned a lot) when you send something they give the sender (the store) a tracking number the sender should give YOU in order for the shipping office (Zoom) in your city to give you the package. (this number is important)
this was my first time buying anything online so i didn’t know any of that just vaguely knew how it worked, so i asked her if she the next day would give me the tracking number or the shipping company would call me when my package was on the shipping center? and she told me “both, i will give you the number and they are going to call you” I said perfect, thank you very much and thought ‘hey that went well!’
Unknown to me, for the next 10 days i was going suffer a weird and painful skin reaction on both hands, and man…it was bad (tw graphic description of a skin condition ahead) the skin on the palm of my hands completely fell off, and it burned like i had scraped my hands on the sidewalk and someone was pouring lemon juice on them. Ouch. as you can imagine all my attention was on what was going on with my hands. I still don’t know what could have caused that severe reaction.
With difficulty texted the woman on Monday 20 i asked again for the tracking number but she said “i’m waiting for the bike delivery guy to give me the number but your package was sent” so she -the store seller- dont go personally to Zoom to send the packages and some else does, i tell the woman again to give me the number as soon as she has it, bc Zoom has an app you can check your package rute and status with that number, she said “okey amiga”.
That week, i could barely lift a fork i was suffering from whatever it was that happened to my hands until my mom found an Aloe Vera plant and i started to rub that gooey, viscose gel thingy on my hands and was slowly getting better, (seriously guys, Aloe Vera plants are a godsend keep one or 10 at home) by the time i suddenly remembered about the package it was Friday 24 the woman didn’t text me anything like she said would do and i didn’t receive any calls either all week, so friday i text her asking again for the tracking number and oh yes finally she has it! My happiness was short lived because……THE PACKAGE WAS RETURNED.
Something occurred and there was an error on the address or something (I triple checked all my personal info was in order before i gave it to her -thanks anxiety!- so i know it was not on me) i was so furious if only the woman had given me the friggin number sooner that week, i would have realized there was something wrong and would have gone to the Zoom on my city where the package was being held before it was returned to the capital. She told me she would send again my package that Friday BUT Zoom only works mon-fri not weekends. Now I need to wait till monday to receive my thing. great.
Monday 27 rolls in and that week i proceeded to text the woman EVERY SINGLE DAY asking if she had sent my package, i hated being a nuisance texting so much but it was necessary, money is getting short and we need food.
On Wed 29 I even texted her a desperate plea, i told her please i need my power supply to start working again! and you know how she responded? BY LEAVING ME ON SEEN. i called her until she answered and she told me “oh i sent it today” she assured me, in the most unsure voice she could muster, that she totally did it.
So I went the next day to the Zoom office and surprise! it was a lie, she didn’t send anything, nada! again asked her for the new track.num. and she told me “amiga the thing is that …the package has not arrived here. is still in your State.“ [*record scratch*] hmm whAT?
I immediately called Zoom and asked them to tell me where my package is? Where is it!?, it’s still in my city or in the Capital?? So they gave me a number for the returned package to check on the app and…said it arrived at the Capital Fri. 24. Not only that but it was marked as "given to the client” aka the sender.
Now I realize this woman has been lying to me. For a whole week. I text her screenshots of where the package was and she tells me that supposedly the package is not on Zoom there and insists it is here in my State. A friend knows someone that works on Zoom that checks their database and confirms that no, is not here anywhere and that definitely arrived in the Capital. even shows that a man named A. Rodriguez was the one that picked up the package. Who is this man?? what's going on?
here's a meme i sent my friends in the group chat while i was trying not to freak out about all this.

This has become a "she-said, he-said" situation because the woman keeps insisting Zoom is the one at fault about the whereabouts of my missing package but Zoom says Hold it! And slaps continuous evidence that shows the places where the package has been at all times.
Meanwhile I’m like “where the hell is my power supply??? All I want is to work. Why is this happening to me?” ;_;
So far what we know:
Package arrived in my city but was returned to the city of origin (the Capital) on Friday 24.
The following week the store seller lied to me and would everyday promise to send the package again to me. and never did.
On Thursday 30 the woman tells me that the package never arrived from my city and she’s waiting for it to “arrive” but the shipping office tells me the package was returned a week ago on Fri. 24 so it’s impossible that it has not arrived. not for nothing they are called ZOOM they deliver fast.
the app even says “given to the client”, and one thing I know for a fact, is that it is near impossible to pick up a package from there without the friggin tracking number, they won’t even give you info about it without it. so it’s very unlikely that a random person just walked away with it.
so we have two possibilities:
1. Someone from Zoom stole it. Ok, feasible. Corrupt people working on this kind of service in my country steal things of value all the time. still i doubt this was the case, the company seemed really concerned and would try their best to help me find my package giving me all the info i requested, even the name of the person who took it.
2. the store seller lied again and the man who took the package is the same bike delivery guy that transported it there in the first place. That's how they were able to take it from there so easily. She denied knowing anyone named A. Rodriguez but she has lied before so i don’t trust her word. To me, this is the more likely scenario for what happened to the package.
February comes and still I have no idea where is my package and the woman keeps making excuses as to why she “hasn’t found it” she again leaves me on seen after I asked for information, next day I called her non stop because now I’m pissed and i want answers, she finally text me that she will send another power supply since she “couldn’t find the first one” no further explanation whatsoever, and tells me will send it on Friday, but remember that Zoom don’t work on weekends so the new package will be staying on the Zoom office until Monday, my friend tells me that is not good what if the thief works there and steals it again? so I asked the woman to send it on Monday and she tells me that only Tuesdays they send all their stuff to be delivered….now she tells me the store have a specific delivery day? Now?
I’m not happy about waiting for more days but there is nothing i can do about it so February 11 is here and I send the woman a text telling her to take a photo of the receipt with the tracking number so the story of the first package won’t repeat, and guess what? The woman left me on seen!! you don’t know how that blue seen mark got me shook. that stressed me so bad that finally I had enough, my friends encouraged me to cancel the order and ask for a refund, I stopped texting her on WhatsApp and left a ultimatum on the Mercado Libre chat, that way I had proof on that page of the fraud this woman was pulling on me and could get her banned there. I should have done that before but the need to repair my computer blinded me and was what kept me trying so hard to get my power supply. Desperation can drive you to make foolish decisions.
After my ultimatum, the woman changed her tune and was very solicitous, and replied super fast, even said on the chat “let it be noted we are a serious company and always answered all your messages” yes, she said THAT, can you believe the audacity, the nerve? I immediately reply “since you didn’t answer any of my texts yesterday, can’t fault me for expressing here my concern about my purchase.” Then I said very politely but with finality that if she did not send me the photo of the receipt with the tracking number the next day I would not hesitate bitch to ask for a refund. And what do you know? Worked like a charm. The next day the first thing in the morning on my phone was a photo of the receipt.
SO yes this unnecessary long story has an anticlimactic but happy end after all! Next morning I happily went to the Zoom office and after a whole month of countless lies, unanswered texts, blood, sweat, and tears, I picked up mypower supply. Reunited at long last! This happened on February 14. Valentine’s Day. Love -and being persistent af- always wins!
TL;DR I bought online a new power supply, the seller tried to scam me or something bc lied about how my purchase was “lost” saying the shipping company was the culprit. Sending me on a wild goose chase trying to find my package. i had to threaten her with a refund to get her to send me finally my power supply.
#this is why i disappeared for a while#can't believe this drama lasted for a whole month#but im glad its finally over
14 notes
·
View notes